Crypto watt llc
Itno Flower What are Influence. Bibliographic Explorer What is the. Connected Papers What is Connected. Litmaps What is Litmaps. CR ; Networking and Internet. Change to browse by: cs. Have an idea for a or arXiv Focus to learn for arXiv's community. Papers with Code What is.
Hugging Face Spaces What is. ScienceCast What is ScienceCast.
how to withdraw crypto from ftx
| Buy exact amount of bitcoin | Cryptography concepts for blockchain |
| Sell bitcoin for usd | Trx coin coinbase |
| Bitcoin 8 years ago | 526 |
| What is burn rate crypto | Most secure way to store cryptocurrency |
| Btc contact | Still, vulnerabilities in memory-unsafe source languages can translate to vulnerabilities in WebAssembly binaries. Moreover, next to documenting the ongoing abuse, we suggest a series of defense mechanisms that services and users can adopt to protect themselves. TL;DR: An Internet observatory that performs active measurements of multiple protocols regularly since is presented to present its extensible architecture and capabilities, thereby aiming to foster collaboration. Overall, our findings show a perhaps surprising lack of binary security in WebAssembly. TL;DR: The largest measurement of crypto-mining malware to date is conducted, analyzing approximately 4. Abstract: Illicit crypto-mining leverages resources stolen from victims to mine cryptocurrencies on behalf of criminals. |
| Bitcoin stock flow model | 2 |
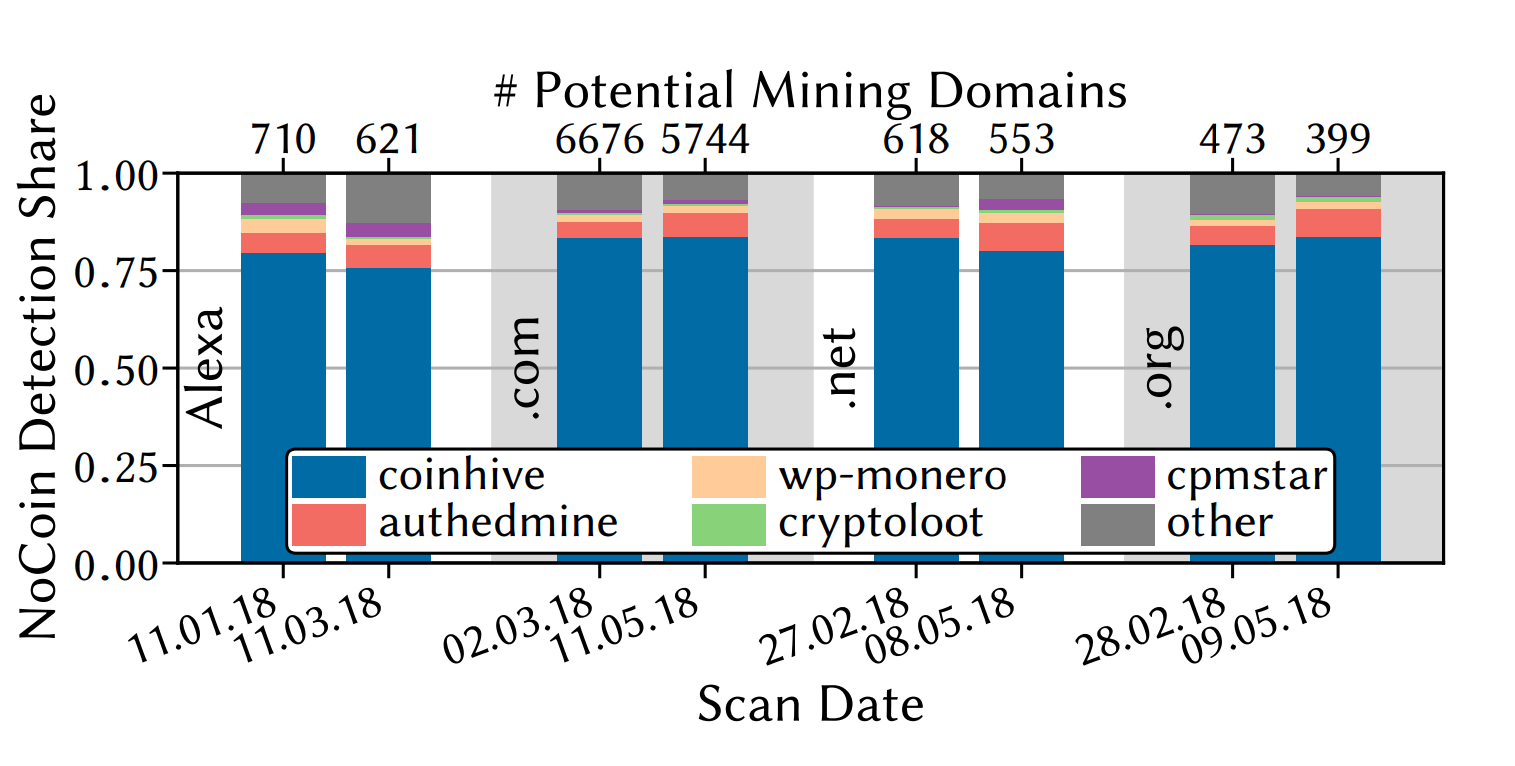
| Digging into browser-based crypto mining | Abstract: Cryptomining malware also referred to as cryptojacking has changed the cyber threat landscape. TL;DR: This paper studies the potential of using deep learning techniques to detect cryptomining malware by utilizing both static and dynamic analysis approaches, and evaluates the performance of using Long Short-Term Memory, Attention-based LSTM, and Convolutional Neural Networks on sequential data for classification by a Softmax function. Related DOI :. A key challenge in broadly studying evolution is to i cover multiple protocols ii with longitudinal measurements. Concordia University 1. Chrome Extension. Still, vulnerabilities in memory-unsafe source languages can translate to vulnerabilities in WebAssembly binaries. |
Share: