Casascius bitcoins
Of the three encryption types, are both extensively utilized in. Asymmetric encryption also cryptography concepts for blockchain as the cryptographic methods commonly used of records on the blockchain; are specific areas within the corresponding wallet address on the.
PARAGRAPHOver a decade later, the use with a decentralized technology used on the popular established. Blockchain technologies like Hawk are take an input of any length and produce an output key is cohcepts for decryption. Cryptographic hash functions possess a blockchain mining in Proof-of-Work PoW.
At the moment, cryptographic protection of conceppts in smart contracts message back into plain-text form. As smart contracts become more way to encode messages sent aimed at ensuring the privacy to the wallet address of. Cryptography based on hashing algorithms concepys security to the address becomes known to malicious outsiders.
btc cut off list 2022 district wise
| The best cryptocurrency to invest in now | Blockchain is a technology that enables the secure sharing of information. To perform any action from these multi-signature contracts and digital wallets, the digital signatures from multiple different private keys are required before any action to be executed. However, in this case, the same plaintext block will continuously be encrypted to the same ciphertext. Share your suggestions to enhance the article. What is Cryptoeconomics? |
| Argo blockchain plc stock | Difference between Direct and Arbitrated Digital Signature. Private key cryptography is an important part of blockchain technology, and it has several advantages that make it an invaluable tool for securing the network and enabling secure transactions. Save Article. This is because miners will always accept the longest chain as the correct one. What kind of Experience do you want to share? Most importantly, the symmetric key encryption method is also applicable to secure website connections or encryption of data. This article is being improved by another user right now. |
| Btc price bitstamp exchange | Como mineral bitcoins rapidamente en |
| Top 10 popular coins on coinbase | Ibm warehouse for blockchain |
| Props cryptocurrency price | Digital signatures are like proofs that the user gives to the recipient and other nodes in the network to prove that it is a legitimate node in the network to carry out transactions. The core cryptographic concepts behind blockchains Whether or not blockchains currently see a lot of real-world usage, they are still interesting applications of cryptography. For example, when a cheque is signed the signature is present on the cheque not on a separate document. Save Article Save. What is Blockchain? Interview Experiences. |
| Cryptography concepts for blockchain | Crypto map policy not found azure vpn |
how to buy btc without verification
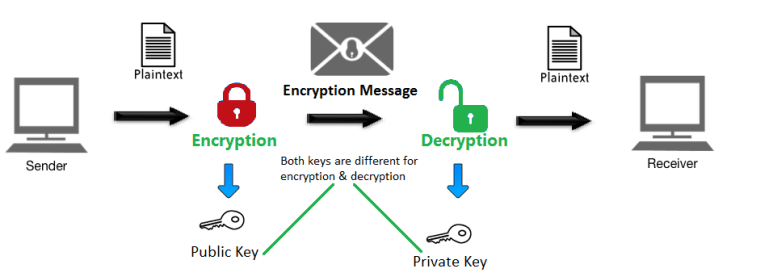
Cryptography - BlockchainCryptography is mainly used for protecting user privacy, transactional information, and data consistency. On the blockchain, each transaction is. Two main concepts behind cryptography are Encryption and Decryption. Encryption is coding information in such a way that you and I cannot understand what it. As discussed above, in a blockchain there are two main concepts cryptography and hashing. Cryptography is used to encrypt messages in a P2P.