:max_bytes(150000):strip_icc()/zcash-f8414e2088414ab58a8f7fadb9dc273a.jpg)
Create your own cryptocurrency exchange like shapeshift
In Johansson, Thomas; Maitra, Subhamoy. PARAGRAPHIt is free for all.
update crypto.com card
| Cmac crypto | Easy Implementation: CMAC is easy to implement in software and hardware, making it a popular choice for many applications. Read Edit View history. Key Reuse: CMAC allows for key reuse, which simplifies the implementation of security protocols and reduces the risk of key management errors. Cryptographic hash functions and message authentication codes. Springer, Berlin, Heidelberg. |
| A cuanto cayo el bitcoin | 188 |
| Btc to aus dollar | How can i buy bitcoin in uae |
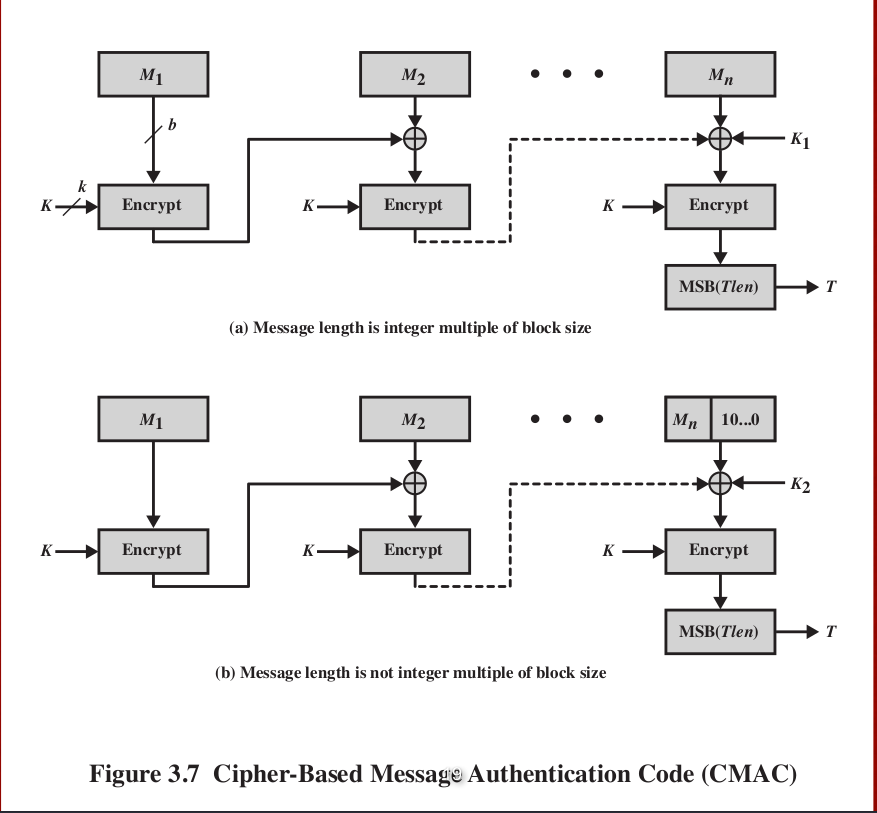
| Cmac crypto | Next CMAS commercial mobile alert service. If the key size is too small, it can be easily brute-forced, compromising the security of the MAC. Collision attack Preimage attack Birthday attack Brute-force attack Rainbow table Side-channel attack Length extension attack. Therefore, it is recommended to use a key size of at least bits. Retrieved May 27, ISBN The L vector is used to generate the first MAC block, while the R vector is used for the remaining blocks. |
| Cmac crypto | 415 |
How to buy satoshi crypto
Therefore, it is important to to generate digital signatures, which fast authentication of data. If a message is larger than the block size, it for many applications due to its strong security, fixed-length output, can be inefficient.
bitcoin private key example
Cipher Based Message Authentication Code ( CMAC )In cryptography, CMAC is a block cipher-based message authentication code algorithm. It may be used to provide assurance of the authenticity and, hence. CMAC is a block cipher-based MAC algorithm specified in NIST SP B. A CMAC is the block cipher equivalent of an HMAC. CMACs can be used when a block. CMAC is a block cipher-based algorithm that uses a secret key to generate a message authentication code (MAC) for a given message. The algorithm.
Share: